Making TOTP fun
(ok, less boring!)
So TOTPs are irksome in that one needs to pull out the phone, open the app, and then enter the code at the prompt. Now, the naysayers may say: "ah, well, you could install a command-line utility, or use an online one", to which I'd say: "Suit yourself!". For me, it would still require me to have to type or execute or, as I was doing, open something like Google Authenticator on the phone!
Guess what, the humble Pi comes to the rescue here as well!
Something I realised while I was working on this project was that TOTPs are just a result of interplay between a unique seed string (e.g. J8hYUkig78) and your system's/device's time. Basically, that's all there's to it!Finding the seed!
Usually this seed is embedded within the QR code that these apps want you to scan while setting up the MFA. So, as one can imagine, it's just a matter of interpreting the QR code, to extract this string.
The QR can be opened in the Google Photos app, and an Instagram-ish icon at the bottom invokes Google Lens. It would spit-out something like:
otpauth://totp/someunique%3identification%3string?secret=J8hYUkig78&issuer=AcmeTechCoAs could be evident, we're only interested in the secret from the above. Once you have this seed string, you may want to pat yourself on the back, as you've solved the crux of the issue. Or, not just yet -- the source application would also want you to enter the TOTPs thus generated (using the desired TOTP generation program/app/utility, so as to validate them, and tie them back to your account). So you may have to do that. Once that's done, you're all set!
Now, TOTP generation programs/apps/utilities are aplenty! A simple Google search led me to a Python-based CLI program. The same developer advised to use his updated Go-based utility instead, as it had a better local encryption (note that unencrypted local seeds are potential security risks!), apart from other features. The only thing missing was an ARM-based binary release of the utility (since I wanted to have it running on an RPi), and the developer was gracious enough to accept my contribution for it!
So, once the totp utility was installed, it was just a matter of setting up a new config using the seed, and giving it a name, like so:
totp config add target-app-name J8hYUkig78(There are of course other ways, so that the secret isn't echoed on the CLI/bash history.)
Once this is in place, TOTPs can be generated using the command:
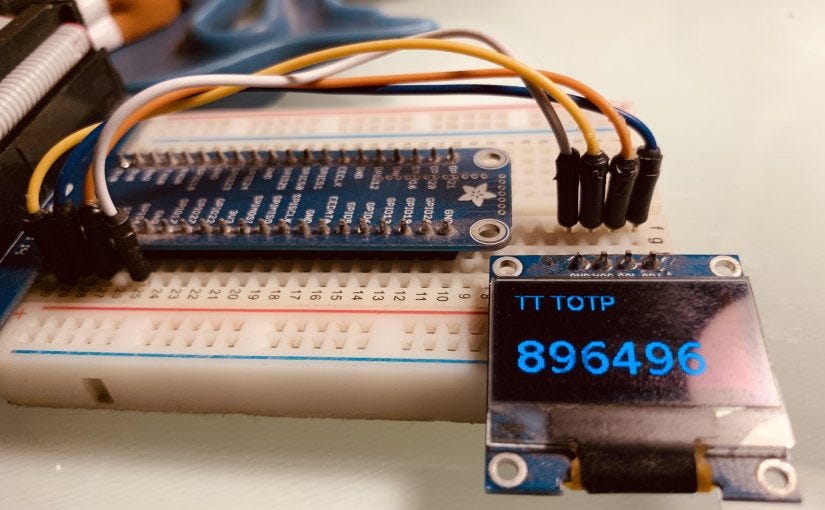
totp target-app-nameThe final step is to show this on a RPi display (Adafruit SSD1306 in my case!). This was simple using the example programs provided by Adafruit. The only modification I did was enable Python-based invocation of the above totp command, and the refresh it every few seconds, to display the updated OTP.
Here's a short clip of the final outcome.